Table of Contents
Originally posted on dt.ua, translated and edited by UaPosition
See also “Hybrid warfare as a key instrument of the Russian revenge geostrategy.”
It is already more than a year Ukraine has been in active phase of the undeclared hybrid war with the Russian Federation. This confrontation is a problem not of a year or two, but obviously the longer period. At the same time the coming years can be decisive.
We have to admit that although Ukraine for 2014 from almost destroyed and demoralized army could create an efficient force, in the prolonged direct confrontation with the substantially stronger opponent the prospects of “weaker” seems to be rather dubious. And Ukraine has objectively less resources (including – financial) and was not preparing for years, unlike our northern neighbor, to this war.
In such circumstances, Ukraine has to use methods that were traditionally tactics of weaker states in the case of resisting aggressive actions of the more powerful states: asymmetric responses aimed to weaken the opponent. However, we must continue to build our own defenses at all possible theaters of war.
This brings us to a problem that has long remained in the general trend of discussion, but the actual practices and integrated public policies in this question are absent, or they have very blurred features: cybersecurity component of national security. After all, cyberspace, whether we want it or not, has become the 5th space of rivalry (including – geopolitical) for all countries.
Cybersecurity component of modern conflicts
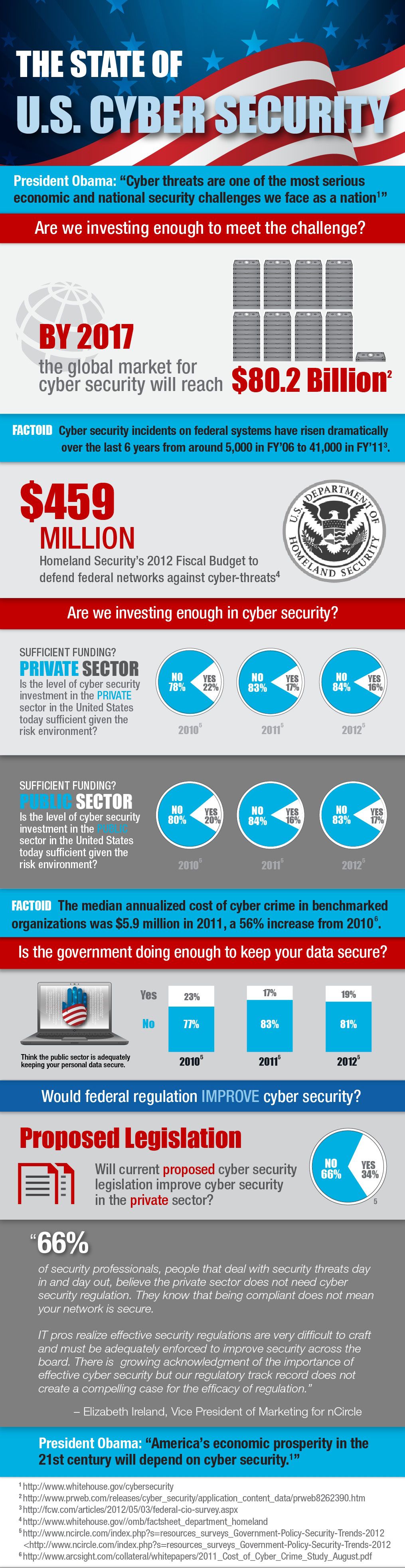
It should be clearly understood that the farther the more the cyberspace as a field of confrontation between two or more parties would gain its value. For today, security agencies budgets of developed countries, involved in cyber security system of the state (and the number of structures that are involved in these processes is constantly increasing), are billions of dollars, and none of the countries have not reduced spending for these items.
Do not be deceived that these funds are invested exclusively in “defense” and “protection” – informally almost all states are developing also offensive cybernetic weapons.
Even as of 2010, experts noted that over 20 countries were developing cybernetic weapons, in 2012 such countries were at least 25. This data is for the period, which is conventionally considered the beginning of the global cybernetic confrontation that today passed a more serious phase, up attempts to cybernetic diversion against the objects of critical infrastructure (particularly in Iran). About the scope and extent of preparation of developed countries to cybernetic confrontation tell also the data of Edward Snowden’s revelatory statements. Although most of that information was already known to experts or they guessed about it, but confirm of those guesses and scope of the programs implemented by the NSA US showed real concern of the US government by cybernetic security issues. It should be borne in mind that the NSA – is not the only US state structure that implements cyber security program, and in general countries that had the financial, human and infrastructure capacity to implement such programs, according to experts, in 2015, were about 140.
It should be recognized that most of the recent active armed confrontations in some way were accompanied with confrontation in cyberspace. It was typical for the recent war in Libya, in part – in Syria, and cybernetic espionage and cybersecurity diversion are generally constant background of international relations. The work of virus Stuxnet, detection of spy viruses and networks Duqu, Flame, Gauss, MiniDuke, Red October, Wiper – these are just a partial list of famous cybernetic espionage or cybersecurity diversion actions that have been found since 2011, and with each passing year they become more and more. And this is without taking into account cybernetic espionage targeted actions against specific government or industrial facilities which purpose – to provide information about closed development (including – the latest research in the field MIC).
It is important to known that virus Stuxnet, the purpose of which was Iran’s nuclear program, its developers saw as an asymmetric response to this program. That means that developed states are acutely aware that cyber weapons can be a real asymmetric tool for resisting to those countries that threaten the existing international security order.
It is difficult to talk about specific proportion of the costs of developed countries to “defense” and “attack” within cybersecurity topics. However, the rate for the second component is much higher than usually say about it. At the time, one of the deputy secretary of defense, William J. Lynn, reflecting on the balance between “defense” and “attack” in cyberspace, correctly noted:
“You do not know how to build reliable protection, you can not avert a major offensive. And you can not provide the required response as an effective deterrent extremely difficult. So, if you want to use cyberspace, you do bet on offensive operations for their own defense.”
We have to recognize that this situation in cybersecurity problems – an objective reality with which we must reckon.
Probably, trying to develop some international control system over cyber weaponry (which is now trying to initiate some countries) or to prohibit their use in destructive purposes for a long time suffer defeat (although it should remain for all of the international community). This is due to several characteristics of the cyber weapons, which often can not be identified as such. In addition, the attack is always cheaper and more harmful to the enemy, and protection – an extremely difficult and worthwhile.
Cyber component of the undeclared war
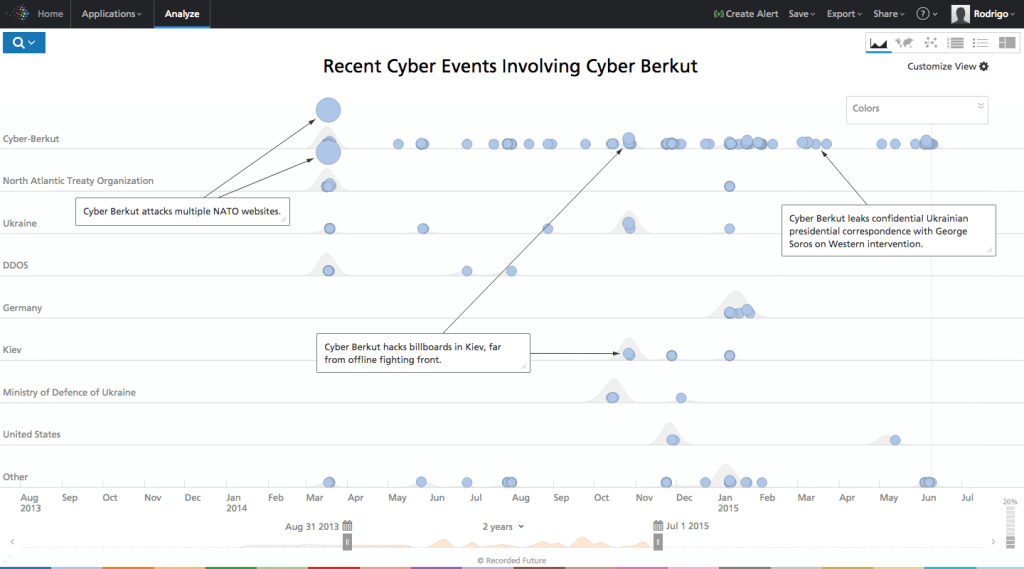
Even after the annexation of the Crimea (and according to some – since Euromaidan) Russia has used cyber attacks as part of a hybrid war against our country. Various “cyberberkuts” from not fully understood “registration” and composition, as well as special units of the security structures of our enemy carried out attacks on government information resources and the personal data of some politicians and public figures. Most known cases of such actions – DDoS-attacks on government resources (MFA, official website of the President of Ukraine, sites of defense and security sector), targeted attacks on state agencies using fraudulent e-mails, the system attempts to violate the CEC during the presidential and parliamentary elections 2014, and the operation of the virus Uroboros, which, with high probability, identified as Russian. It had all the signs of use cyber espionage action against Ukraine, and the virus acted on the web resources of public authorities (including power structures), media, financial institutions, large industrial enterprises.
Data by Recorded Future
And this is with a background of dozen other attempts to influence the security of our state through cyber attacks. For example, according to research company ESET, against Ukraine (and partly – Poland) was used deliberately virus BlackEnergy, whose purpose – to collect data from hard drives damaged computer screens users take screenshots, capture the data entry and more. Tentatively, it affected government organizations, business structures and industrial sector. In addition, against the Ukrainian institutions virus was used CosmicDuke (modified virus Miniduke, whose purpose – stealing information). There are some data on the use of virus FireEye to spy on Ukrainian officials. And this is without taking into account indirect cyber attacks with the help of social networks with thousands of fake accounts to spread false information about events in the country and provoking riots and attacks from the more traditional means of social engineering.
So one of the deputy head of the Presidential Administration of Ukraine, Dmytro Shymkiv, rightly said in a recent interview:
“We are faced with an extremely serious problem of cybersecurity … fend off cyberattacks should be able to.”
Cyber espionage or cyber diversion actions today cause damage to our defense.
It is no secret that Russia’s secret services used the power of some of the largest Ukrainian mobile operators in order to listen to Ukrainian phone subscribers to determine their location, receive all necessary metadata users. This information is used by a variety of ways: by putting psychological pressure and the use of the data for the guidance aggressor artillery positions on the Ukrainian military in the area ATO.
Actually, today we have examples of using by aggressor the cyberspace (telecommunications component) in destructive purposes against Ukraine. As for now it is limited by cyber espionage actions or DDoS-attacks. But is there any assurance that cyber attacks will not become more serious and not directed to critical infrastructure, making a real threat to life and health of a significant number of Ukrainian citizens? Especially that 2015 will not be more relaxed – even now Ukrainian security structures and expert predict the possibility of growth in the number and quality of cyberattacks against Ukraine. After all, Russia has consistently uses our country as a testing ground not only for testing of kinetic weapons and new tactics of warfare, but also to optimize their own cyber offensive opportunities.
Accordingly, the protection of the state’s cyberspace from attacks, from using it against the interests of national security and defense is one of the priorities for the state. And decisions must be uncovered now, but attention of the state to cyber problematic should move from the plane of theory in practice.
In addition, we must clearly understand that cyberspace must become the tool of our asymmetric response to aggression. At the time, the former head of National Intelligence Mitch McConnell noted that cyber moderation can serve the purposes of building a secure cyberspace, and the presence of powerful cyber offensive potentials can serve as deterrent factor in the application of large-scale cyber attacks against the US.
Ukraine simply not only can, but is forced to stand in a similar position and stop focusing solely on defensive measures. With one of the world’s best human development, IT professionals, the ability to work quickly and efficiently, highly motivated opposition to external aggression, the state should bet not only on defense technology, but also on the offensive, including – cyber weaponry. The enemy should know that trying to use cyberspace to the detriment of the national interests of Ukraine, he may face a massive cyber reply. This, in turn, will increase its spending on defense, which may be one of the aims of asymmetric response. The said clearly contradicts all peacekeeping activities undertaken at the global level, the demilitarization of cyberspace, but we can no longer pretend not to notice the reality in this area, replacing it with ineffective talks.
Focus on the development of cyber weaponry is important in one more reason. We always call on our Western partners to provide us with lethal weapons for defense against external aggression. However, at the same time we don’t use even those opportunities that we have. We must honestly admit that getting arms from the West – the question ambiguous, and assistance in creating our own offensive capabilities we will most likely not receive. Similarly is for cyber weaponry. But last we can really create by ourselves basing on own potential and the same opportunities. It does not reject our cooperation with Western allies in building the cyber defensive opportunities, but cyber offensive – area of responsibility only Ukraine itself.
Condition and perspectives of the cyber security sector of Ukraine
Until recently, the development of the cyberspace sector in Ukraine was quite specific, and sometimes – fragmented. Of course, these questions were quite “in the air” – in varying degrees to meet the challenges in this area involved many government agencies, main of which are DerzhSpetsZv’yazok (State Service for Special Communications and Information Protection of Ukraine), Security Service, Interior Ministry and defense and intelligence structures within their tasks and powers.
However, despite all the systems in these processes are still little, and effective coordination of activities difficult to speak. And for this there are a number of objective and subjective conditions.
First of all, it is still unclear who is actually responsible for cyber security theme in the country. Since 2011 has been made many attempts to resolve the issue at the legislative level, including – within relevant law of Ukraine. The task to develop such law has appeared regularly in the decisions of the National Security Council (the last time – in the May decision in 2014, focused on information security), but still wasn’t much progress in this regard. We must honestly admit that one reason for this – the presence of interdepartmental contradictions and complexity of compromise between the state structures. Each institution is not willing to give up his interests and powers, considering that it must become a “key” structure. In most cases this discussion concludes that there is the need to create a completely new state structure that will take care of cybersecurity issues. Titles for it have been enough already invented – the from “Cyber Service” to “Agency of cybersecurity of Ukraine.”
Formally, the “lawyers” of this idea are right: global experience shows that in most of these structures are in most countries, in these states is built tough model of management in cybersecurity national sphere. However, the “world experience” – something interesting: in it, as in the Bible, you can find answers to almost every taste and for every occasion. Perhaps, except one – which should be a system of cybersecurity for the state that actually, not theoretically is in the active war against the more powerful enemy?
And the question arises: whether the country’s situation is so stable, and the budget – so much money that the state can afford such a large-scale reform (and with rather ambiguous end result)? It is not about “changing signs” and a serious redistribution of functions and formation of new structures.
In private conversations functionaries of NATO who deal with cybersecurity when they hear about the need to “create a framework” or ” thoroughly redistribute powers of acting sides,” rightly ask: “Do you really have a war that you have time for such things?” . Today Western partners are ready to help us in building our country’s cyber defense, but not in the sponsoring simulation institutional reforms that only slow time. And in such assistance that NATO is still extremely specific: for this purpose after the NATO summit in Wales in 2014 established a special trust fund to address the cybersecurity Ukrainian state.
But for this we need to decide who will be the one structure, which will assume responsibility for coordinating of cyber security sector. Objectively, it may not be immediate security sector and defense, since none of them has the authority and capacity to cover the whole range of issues. Perhaps it would be putting additional powers to coordinate Ukraine’s NSDC, especially after the recent rule-making activities its powers expanded. However, within the Ministry of Defence establishment of cyber command also seems appropriate, especially considering the fact that today’s cyber defense and cyber functions in this structure are dispersed among several departments.
Other critical issue is strategic planning in cybersecurity. Still there is not even a general document on the strategic vision of the state cybersecurity theme. Traditional for all developed countries in the world document “Cybersecurity Strategy” (under different names in different countries) is still not accepted, although such attempts were made at least from 2012 till 2014 The objective of this Strategy – to answer questions on key threats to national security in cyberspace policy priorities in this area, and basic steps to be taken to neutralize threats. And, as in many other areas of state security policy, we have lack of coordination even of available resources. For example, we have at least a few government programs that deal with issues of IT, but their mutual concordance is rather conventional.
Another important problem which the government preferred not to remember a long time is the interaction between state and non-state structures. De facto, the most effective as well as project legal and regulatory initiatives based on the principles of exclusive subjectivity state, while leaving the private sector and fulfills the role of extras ascribed all the documents. In fact, the private sector, despite the fact that the vast majority of critical infrastructure (especially information) belonging to it, is not perceived by the state as an equal partner, and even more – assistant to strengthen the country’s defense in cyberspace.
It is difficult to say how the situation has changed in the last year. On the one hand, one can observe the growth of the openness of state structures for cooperation. At least some initiatives in this direction demonstrate also Derzhspetszv’zok (including – in the face of CERT-UA, Computer Emergency Response Team of Ukraine), and the Security Service. However much cooperation mechanisms are not established, in particular through the existing bureaucratic procedures that do not allow fully engage this potential. It must be recognized that often various “cyber guard” can do what is unable (for various reasons) to be done by state. Although the “cyber guards” (like “Ukrayinski kiberviyska”) understand all the “specificity” of its activity in terms of the Criminal Code.
Finally, the state should optimize the use of available scientific, technical and human capacities for these areas. The key to a successful defense against cyber attacks and strengthen its position in cyberspace – people. These are highly educated professionals who understand the complexity of their tasks. In Ukraine this resource is – annually produced tens of thousands of IT professionals, the level of training many of them meets the world’s. Meanwhile, Ukrainian engineers and programmers create fully competitive software and hardware products that can be used, including, for strengthening cybersecurity state.
However, whether the state uses this resource fully? Unfortunately, in many cases, the “state” and “science” in this area do not overlap or intersect rather arbitrary. On the one hand, this is due to the inability of the state to ensure the objective of attracting many highly skilled professionals into the civil service through lack of adequate funds. It is significant that when CERT-UA recently announced a set of hackers and reported that the expected salary will be about 3.5-5 thousand. UAH, it turned out – the patriotism of many experts does not reach so far as to work for a smaller amount than in the civil service. It is a problem that should be solved. Maybe it must be done through the formation of a special unit within the structure of a state with the appropriate level of payment experts. And no question that there is a hundred specialists work at once – let it be extremely small number of young professionals who have passed a series of national cyber competitions (in most developed countries it is one of the sources of search specialists) and proved its high level and profession.
Generally, it should be taken seriously to various measures to promote the interest of young people of cyber security problematic. We need as already mentioned national cyber competitions and regular hackathons and other events where security agencies will be able to choose for themselves young professionals on a real competitive basis.
At the same time it must be found a more effective form of use of domestic software and technical developments in development of the state’s cyber secutrity potential. Immediately several powerful universities of Ukraine prepare highly qualified specialists and already have the appropriate technical achievements that may be introduced in the domestic sector cybersecurity. Actually, it is about the formation of complex software and construction functioning of the state system of Ukraine cyber security.
There are different ways to assess current readiness of the state to conduct an active phase of armed confrontation with the aggressor, but cyberspace – this is the place where we really can and should give a fitting rebuff to the enemy. Cyberspace has to become one element of an asymmetric response to aggression, efficient front of our resistance. The state has for this almost everything needed, and what doesn’t have the state – have its citizens. So our task here and now – to use this resource, providing the necessary institutional, legal and practical approach changes of the state to cybersecurity problem.